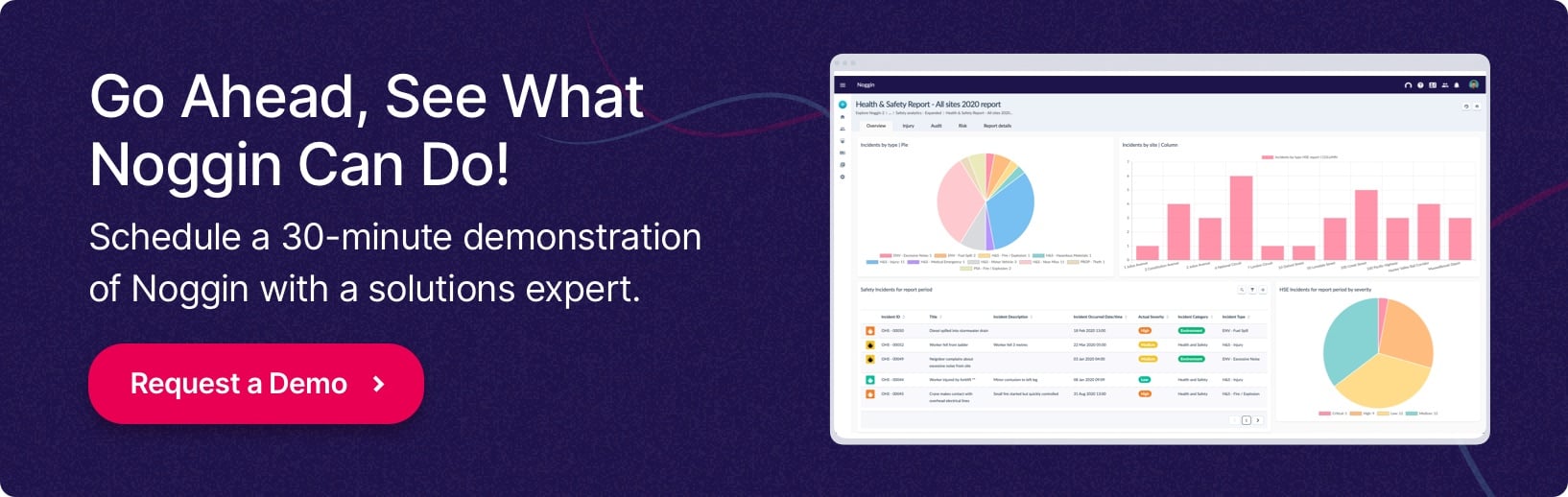
Request a Demo
Fill in the form below and we will contact you shortly to organised your personalised demonstration of the Noggin platform.
Meet Noggin
An integrated resilience workspace that seamlessly integrates 10 core solutions into one, easy-to-use software platform.
The Noggin Platform
The world's leading integrated resilience workspace for risk and business continuity management, operational resilience, incident & crisis management, and security & safety operations.
Industries
Explore Noggin's integrated resilience software, purpose-built for any industry.

A Resilience Management Software Buyer's Guide
Whitepaper
Guide to Improving Cyber Incident Response and Management
Noggin
Security Management Software
Updated July 12, 2023
Table of Contents
The cyber risk picture deteriorates
The cyber risk picture has never been darker. Most urgently, the rapid upsurge in remote worki resulting from the pandemic has coincided with a massive uptick in cyber attacks.
Already in March 2020, online threats had risen by as much as six times their February 2020 levelsii. Hacking and phishing attempts alone were up 37 percentiii. Cloud-based attacks ballooned 630 percent between January 2020 and April 2020iv. By the end of the first half of 2020, 4.83 million distributed denial of service (DDoS) attacks had been attemptedv.
From there, the surge in cyber attacks only got worse. By June 2020, reporting found a staggering 400 percent increase in cyber attacksvi. By August 2020, 80 percent of companies were reporting an annual increase in cyber attacksvii. Banks saw a 238 percent increaseviii.
Finance wasn’t alone. The global healthcare sector also became a preferred target. In April 2020, the WHO confirmed a dramatic increase in the number of cyber attacks directed at its staff, as well as email scams targeting the public at largeix.
Besides the WHO, a high-profile IT incident involving a Czech Republic hospital ground that country’s COVID-19 testing effort to a temporary haltx . The U.S. Department of Health and Human Services was also the victim of a foiled DDoS attackxi.
All-of-government attacks gained in popularity, as well. Prime Minister Scott Morrison announced that Australia had been the target of coordinated cyber attacks against its public infrastructure, breaches that crippled vast networks and affected essential servicesxii.
Late in 2020, the then-outgoing Trump Administration revealed that U.S. governmental institutions had been hit by a massive cyber campaign, when hackers gained access to a Texas-based IT company, SolarWindsxiii. Nearly 20,000
of SolarWinds’ public and private-sector clients might have been exposed, highlighting the vulnerability in third-party resources – 23 percent of those assets have at least one critical vulnerabilityxiv.
Of course, the volume of cyber risks was accelerating even before the pandemic. Often-overlooked, insider threats have increased over the last few years. From 2018 to 2020, insider threats jumped by 47 percentxv. More worrisome still, up to 70 percent of those attacks might not have been reported externallyxvi.
In turn, costs have soared. In 2020, ransomware demands, the third most popular type of malware used in breaches, came in at a cumulative USD 1.4 billion, with an average sum to rectify damage reaching USD 1.45 millionxvii.
Penalties stiffen for ineffective response to cyber incidents
Why does it matter? Not only do these incidents have steep reputational, productivity, and financial costs of their own. A poor response might also trigger increased compliance activity, often coming with a hefty monetary penalty.
Indeed, over the last decades, governments and sectoral regulators have sought to shore up the digital privacy of their citizens and consumers. Legislative schemes like the General Data Protection Regulation (GDPR) in the European Union, the Privacy Act in Australia, and the California Consumer Privacy Act have all been attempts to enhance privacy rights and consumer protections.
Each of the schemes impose steep fines for records breached, ranging from USD 7500 per record in California to up to 10 percent of a breaching entity’s annual national turnover in Australia.
But the GDPR, which has the greatest footprint, also places a timely notification window on breached entities to reveal publicly that they’ve been breached. Per Article 33 of the GDPR, notification of a personal data breach must be made to the Supervisory Authority; here are the particulars:
- In the case of a personal data breach, the controller shall without undue delay and, where feasible, not later than 72 hours after having become aware of it, notify the personal data breach to the supervisory authority competent in accordance with Article 55, unless the personal data breach is unlikely to result in a risk to the rights and freedoms of natural persons. Where the notification to the supervisory authority is not made within 72 hours, it shall be accompanied by reasons for the delay.
- The processor shall notify the controller without undue delay after becoming aware of a personal data breach.
- The notification referred to in paragraph 1 shall at least:
a. Describe the nature of the personal data breach including where possible, the categories and approximate number of data subjects concerned and the categories and approximate number of personal data records concerned;
b. Communicate the name and contact details of the data protection officer or other contact point where more information can be obtained;
c. Describe the likely consequences of the personal data breach;
d. Describe the measures taken or proposed to be taken by the controller to address the personal data breach, including, where appropriate, measures to mitigate its possible adverse effects. - Where, and in so far as, it is not possible to provide the information at the same time, the information may be provided in phases without undue further delay.
- The controller shall document any personal data breaches, comprising the facts relating to the personal data breach, its effects and the remedial action taken. That documentation shall enable the supervisory authority to verify compliance
with this Article.
The GDPR, here, isn’t just relevant, because it covers the most data subjects. The GDPR has also been taken as the model for proposed changes to statutes in other jurisdictions hoping to bring their timely notification windows into alignment with the more stringent obligation in the GDPR.
Besides sanctions for consumer protection violations, governments are also hardening cyber resilience standards across the board. For instance, Australia is in the process of updating its Security of Critical Infrastructure Act to add enhanced cyber security obligations on regulated sectors. Those obligations would establish:
- The ability for the Government to request information to contribute to a near real-time national threat picture
- Owner and operator participation in preparatory activities with Government
- The co-development of a scenario-based “playbook,” setting out response arrangements
The-above cyber security obligations go above and beyond those set in the positive security obligation (PSO), another feature of the amended Act. That PSO will obligate regulated entities to manage risks that may impact their business continuity, risks which include cyber risk. Mitigating cyber risk, specifically, entails:
- Identifying and assessing sensitive information and implementing proportionate controls
- Understanding access to an entity’s sensitive information, with need-to-know principles applied
- Endeavouring to safeguard information from common and emerging cyber threats and adhering to best practice guidelines
- Implementing robust security measures during all stages of ICT systems development
- Aiming to ensure systems and personnel can detect, understand, and respond to cyber security incidents
Key challenges to effective cyber incident response, with an emphasis on information management
Ensuring that systems and personnel can detect, understand, and, most importantly, respond to cyber incidents, however, involves creating and deploying structured methodologies to efficiently handle cyber security incidents, breaches, and threats. That’s not easy. Adding public notification requirements on top of that makes it even harder. Nor is compliance the only challenge to effective cyber incident response. Here are just a few:
-
Too many incidents.
The sharp rise in cyber incidents means that individual organisations, especially those in socalled critical infrastructure sectors, are dealing with more cyber incidents than ever.
Alert fatigue is real. Add to that, not all alerts will be the big one. The rapid acceleration in alerts, therefore, might compromise the ability of an organisation to respond effectively to a serious breach. -
Incident response plans (IRPs) are too generic.
Guidance on how to respond to cyber incidents is prolific. Government agencies like the Cybersecurity and Infrastructure Security Agency (CISA) and National Institute of Standards and Technology (NIST) all publish their own expert advice.
Organisations are free to make use of that guidance. But simply copying and pasting those plans wholesale, which many organisations do, might not be the best idea. By their very nature, one-size-fits-all IRPs aren’t tailored to the needs and specificities of individual organisations. They can’t, therefore, account for differences in organisational culture, environment, response, personnel, and business objectives. -
Plans are untested.
The rubber really hits the road for these generic IRPs during a crisis. Generic plans are less likely to be tested before a real-world incident, where regular testing would expose flaws in assumptions.
Oftentimes, customised plans aren’t tested, either. Which means many haven’t been updated to account for the transition to remote working, where key personnel are geographically dispersed, unable to review logs, detect attacks, respond to and recover from incidents as they might have formerly. -
Information doesn’t get to the right people at the right time.
These arrangements also pose grave communication and collaboration challenges for effective cyber incident response, though it’s not as if information easily got to the right people at the right time before the pandemic.
Indeed, information management has long been cited as one of the starkest challenges to effective cyber incident response and management. It’s not hard to see why. Providing intelligence, coordination, and response that is accurate, timely, and effective requires the coordination of a number of processes, systems, and operators.
This can be difficult. Requests might require novel approaches, integration of disparate data sources, including contributing information systems, and a wide variety of outputs. Not simple when teams, especially IT security, are unnecessarily segmented.
What happens then is data pertinent to the incident isn’t made available to decision makers, whether in Incident Response or in the C-suite. When it is made available, information is strewn across hundreds of emails – often duplicative, making it well-nigh impossible for decision makers to task effectively throughout the lifecycle of a cyber incident based on a cohesive picture of what’s happening.
These information management challenges have a further consequence, when it comes to generating reports (e.g., closure, post-incident, advisory, insight, and/or executive summary) for internal stakeholders, customers, partners, regulators, or others. Add to that: the spectre of timely notification requirements looms in certain jurisdictions and sectors.
Role of digital technology in improving cyber incident response and management
So, what’s there to be done, especially if your organisation finds itself heavily reliant on email for executing your cyber security IRP? We recommend finding a flexible, configurable, digital solution that helps plan and manage your information, operations, and communications.
Such a solution would capture and consume information from multiple sources, including reports, logs, communications, forms, assets, and maps, providing a realtime common operating picture of the task or operation at hand.
Leveraging powerful, yet easy-to-set-up workflows, the user-friendly solution would control and automate management processes and standard operating procedures, keeping the right stakeholders informed across multiple communications mediums. Analytics and reporting tools would ensure that decision-makers have the correct information in the best available format, when they need it. The solution would also track tasks to ensure that the right actions are taken and followed through, helping you to assign, manage, and track resources.
More specifically, the system would provide a case management framework that orchestrates information flows throughout the organisation, providing consistency where multiple systems, sources, and processes are employed, as well as enabling the secure exchange of information and coordination of resources across multiple stakeholders, who themselves might have varying security constraints.
On top of those information and strategic incident management capabilities, specialist intelligence application benefits would include:
- Reinforce intelligence tasking and response with an auditable record of changes
- Powerful workflow builder to automate review, approval, escalations, and interactions across the organisation and externally
- Ability to relate assets, events, contacts to provide a complete picture of requests, incidents, and tasks, including mapping for geospatial information, timelines for understanding changes and progressions in context, as well as alerts to automatically flag issues for further attention
- Configurable dashboards that provide an executive view of progress, emerging issues and crises
- Support for scalable processes to handle routine or commodity threats through to Advanced Persistent Threats (APT)
- Support for intelligence gathering for entities of interest including evidence gathering and multiparty coordination
- Configurable security model to accommodate low privilege users, such as third-party IT staff to log threats and incidents or receive reports without gaining access to more sensitive information
- Asset inventory and logging to highlight prioritised assets or other high impact items.
Finally, cyber breaches are rising by the day, as hackers get even better at exploiting vulnerabilities. For their part, policymakers have stepped up, tightening provisions for consumer data protections and hardening cyber resilience mandates for regulated entities.
Part of these mandates consists in improving cyber incident response capabilities, though. Of course, responding to cyber incidents isn’t easy. The information management challenges associated with cyber incident response alone are prodigious. What can help alleviate those challenges, ensure compliance, and enable better cyber incident response: digital platforms, like Noggin’s, that can effectively orchestrate information flows, provide consistency where multiple systems, sources, and
processes are employed, and enable a secure, controlled exchange of information and coordination of resources.
Citations
i University of Arkansas, ScienceDaily: Pandemic accelerated remote work, a trend likely to remain. Available at https://www.sciencedaily.com/ releases/2020/09/200902152130.htm.
ii Phil Muncaster, Infosecurity Magazine: Cyber-Attacks Up 37% Over Past Month as #COVID19 Bites. Available at https://www.infosecurity-magazine. com/news/cyberattacks-up-37-over-past-month/
iii Ibid.
iv Fintech News: The 2020 Cybersecurity stats you need to know. Available at https://www.fintechnews.org/the-2020-cybersecurity-stats-you-needto-know/.
v Juta Gurinaviciute, Security Magazine: 5 biggest cybersecurity threats. Available at https://www.securitymagazine.com/articles/94506-5-biggestcybersecurity-threats.
vi Rick Smith, WRAL TechWire: Reports: Cybercrimes surge 400%, teleworkers need to tighten security. Available at https://www.wraltechwire. com/2020/06/25/reports-cybercrimes-surge-400-teleworkers-need-to-tighten-security/.
vii Fintech News: The 2020 Cybersecurity stats you need to know. Available at https://www.fintechnews.org/the-2020-cybersecurity-stats-you-needto-know/.
viii Ibid.
ix World Health Organization: WHO reports fivefold increase in cyber attacks, urges vigilance. Available at https://www.who.int/news-room/detail/23-04-2020-who-reports-fivefold-increase-in-cyber-attacks-urges-vigilance.
x Catalin Cimpanu, ZDNET: Czech hospital hit by cyberattack while in the midst of a COVID-19 outbreak. Available at https://www.zdnet.com/article/ czech-hospital-hit-by-cyber-attack-while-in-the-midst-of-a-covid-19-outbreak/.
xi Shira Stein & Jennifer Jacobs, Bloomberg: Cyber-Attack Hits U.S. Health Agency Amid Covid-19 Outbreak. Available at https://www.bloomberg.com/ news/articles/2020-03-16/u-s-health-agency-suffers-cyber-attack-during-covid-19-response.
xii BBC News: Australia cyber attacks: PM Morrison warns of ‘sophisticated’ state hack. Available at https://www.bbc.com/news/worldaustralia-46096768.
xiii Hannah Murphy, Financial Times: US agencies say Russia was likely behind massive cyber attack. Available at https://www.ft.com/content/e61325daa0ae-47fe-99bf-b10f61b2658f.
xiv Juta Gurinaviciute, Security Magazine: 5 biggest cybersecurity threats. Available at https://www.securitymagazine.com/articles/94506-5-biggestcybersecurity-threats
xv Deyan G., Tech Jury: 20 Insider Threat Statistics to Look Out For in 2020. Available at https://techjury.net/blog/insider-threat-statistics/#gref
xvi Ibid.
xvii Juta Gurinaviciute, Security Magazine: 5 biggest cybersecurity threats. Available at https://www.securitymagazine.com/articles/94506-5-biggestcybersecurity-threats.